Last Updated on May 27, 2024 by Arnav Sharma
What is Microsoft Defender for Identity?
Microsoft Defender for Identity, also known as MDI, is a cloud-based solution from Microsoft designed to protect an organization’s Active Directory environment. Previously, Microsoft Defender for Identity was known as Azure Advanced Threat Protection and was commonly referred to as Azure ATP.
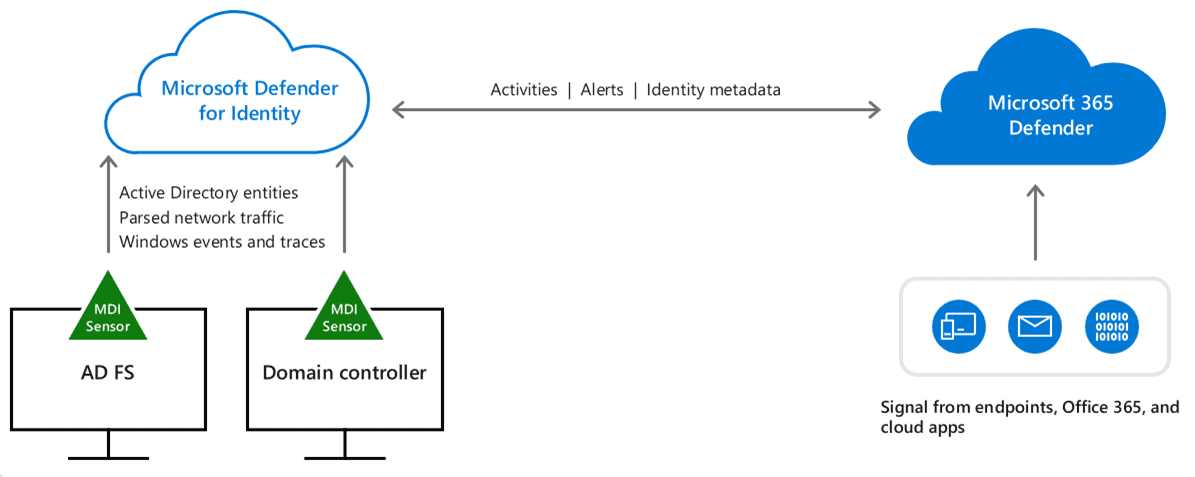
MDI leverages on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at an organization
Why MDI !!
It helps enable SecOps analysts and security professionals to detect advanced attacks in hybrid environments to be able to:
- Monitor users, entity behaviour, and activities with learning-based analytics
- Protect user identities and credentials stored in Active Directory
- Identify and investigate suspicious user activities and advanced attacks throughout the kill chain
- Provide clear incident information on a simple timeline for fast triage
MDI Integration with other services:
- Defender for Identity integrates into Microsoft 365 Defender
- Defender for Identity integrates into Microsoft Defender for Cloud Apps (formerly Microsoft Cloud App Security)
- Microsoft Sentinel has a data connector available for Defender for Identity.
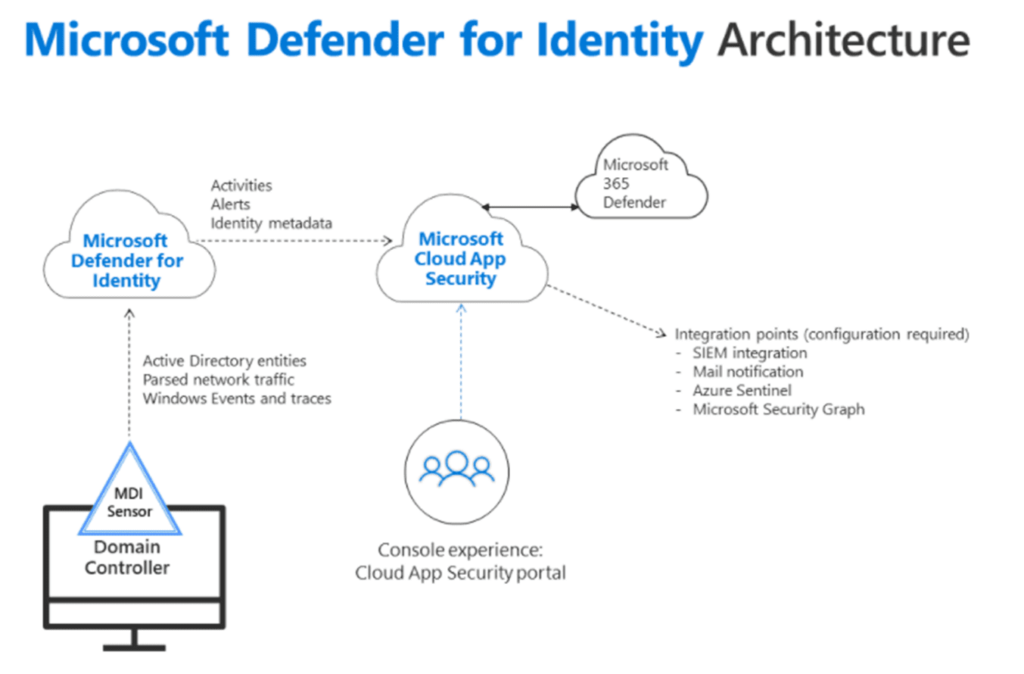
Onboarding Defender for Identity
Prerequisites
- Licensing : EMS E5/A5/G5, M365 E5/A5/G5
- This is a cloud service that works against on-premises Active Directory services or Multi-forest and multi-domain support
- The MDI sensor requires a service account to run, and the recommendation is to use a group-managed service account, also known as a gMSA.
- Audit & Windows Event logging enabled
Steps:
- Go to https://portal.atp.azure.com
- Create the MDI service account in Active Directory (Script below)
- Input the service account information into the MDI portal
- Download the MDI sensor installation files and copy the access key
- Deploy to all Domain Controllers and/or AD FS servers
gMSA:



Alerts & Monitoring:
- Defender for Identity provides reconnaissance alerts, helping identify unusual directory enumeration.
- Defender for Identity provides for compromised credential alerts, helping identify account compromise and threats attempting to gain credentials.
- Defender for Identity provides for lateral movement detection, alerting on common mechanisms.
- Defender for Identity provides for domain dominance detection, which provides insight into malicious actors have gained privileged access to Active Directory.
- Defender for Identity provides for exfiltration detection, which provides insight into malicious actors attempting to exfiltrate data from domain controllers or compromise DNS.

PS Script for creating gMSA and enable access (reboot system in case of error & rerun):
# Set the variables:
#Name of the account - to be cretaed
$gMSA_AccountName = 'mdiSvc01'
#group that will be created for the account created in above step
#Can be any name
$gMSA_HostsGroupName = 'mdiSvc01'
$Identity = 'arnavsharmamdiSvc01'
#name of the domain controller - the target
$gMSA_HostNames = 'WIN-TE2RL78F23R'
# Declare the *user* or *group* that needs to have read access to the deleted objects container
# Note that if the identity you want to grant the permissions to is a Group Managed Service Account (gMSA),
# you need first to create a security group, add the gMSA as a member and list that group as the identity below
# Import the required PowerShell module:
Import-Module ActiveDirectory
#Add a root key
Add-KdsRootKey –EffectiveTime ((get-date).addhours(-10))
#10 hours - back date
Start-Sleep -Seconds 10
# Create the group and add the members
$gMSA_HostsGroup = New-ADGroup -Name $gMSA_HostsGroupName -GroupScope Global -PassThru
$gMSA_HostNames | ForEach-Object { Get-ADComputer -Identity $_ } | ForEach-Object { Add-ADGroupMember -Identity $gMSA_HostsGroupName -Members $_ }
# Or, use the built-in 'Domain Controllers' group if the environment is a single forest, and will contain only domain controller sensors
# $gMSA_HostsGroup = Get-ADGroup -Identity 'Domain Controllers'
# Create the gMSA:
New-ADServiceAccount -Name $gMSA_AccountName -DNSHostName "$gMSA_AccountName.$env:USERDNSDOMAIN" -PrincipalsAllowedToRetrieveManagedPassword $gMSA_HostsGroupName
Start-Sleep -Seconds 10
# Install the gMSA account
#Install-ADServiceAccount -Identity $gMSA_AccountName
# Get the deleted objects container's distinguished name:
$distinguishedName = ([adsi]'').distinguishedName.Value
$deletedObjectsDN = 'CN=Deleted Objects,{0}' -f $distinguishedName
# Take ownership on the deleted objects container:
$params = @("$deletedObjectsDN", '/takeOwnership')
C:WindowsSystem32dsacls.exe $params
# Grant the 'List Contents' and 'Read Property' permissions to the user or group:
$params = @("$deletedObjectsDN", '/G', "$($Identity):LCRP")
C:WindowsSystem32dsacls.exe $params
Start-Sleep -Seconds 10
# Install the gMSA account
Install-ADServiceAccount -Identity $gMSA_AccountName
Start-Sleep -Seconds 10
Test-ADServiceAccount -Identity $gMSA_AccountName
FAQ
Q: What is Microsoft Defender for Identity?
A: Microsoft Defender for Identity, formerly known as Azure Advanced Threat Protection (ATP), is a cloud-based security solution that uses various data sources to monitor user activities and detects security threats on the network in near-real-time to safeguard identities in the cloud and on-premises.
Q: What type of threats can Microsoft Defender for Identity detect?
A: Microsoft Defender for Identity monitors and detects several types of advanced attacks, including MITRE ATT&CK techniques, unauthorized access, privilege escalation, Azure Active Directory (AD) attribute manipulation, and more.
Q: Is Microsoft Defender for Identity a part of Microsoft 365?
A: Yes, Microsoft Defender for Identity is a part of the Microsoft 365 Defender suite of products.
Q: What is the role of Microsoft Defender for Endpoint in Microsoft Defender for Identity?
A: Microsoft Defender for Endpoint works with Microsoft Defender for Identity by providing endpoint protection, enabling organizations to identify and mitigate attacks across endpoints, including Windows, macOS, and Linux devices.
Q: What is the Defender for Identity sensor, and do I need to install it?
A: The Defender for Identity sensor is a lightweight software component that provides visibility into activities that occur on your network. You need to install the sensor on a domain-joined device in your network to use Microsoft Defender for Identity.
Q: How do I configure Microsoft Defender for Identity after installation?
A: To configure Microsoft Defender for Identity, you need to connect the sensor to the Microsoft Defender for Identity cloud service and configure the security updates, technical support, and identity protection settings according to your organization’s requirements.
Q: How does Microsoft Defender for Identity help protect my organization’s identity security posture?
A: Microsoft Defender for Identity helps enhance your organization’s identity security posture by providing continuous monitoring, advanced analytics, security alerts, and recommendations to improve your security posture. It also enables you to analyze and investigate threats and alerts related to identity.
Q: What kind of data does Microsoft Defender for Identity monitor and collect?
A: Microsoft Defender for Identity monitors and collects data related to network activities, Active Directory, cloud apps, authentication events, and other identity-related data to detect and mitigate threats.
Q: How does Microsoft Defender for Identity integrate with Microsoft 365 Defender portal?
A: Microsoft Defender for Identity integrates with the Microsoft 365 Defender portal, providing a unified experience to manage and investigate threats across various Defender solutions.
Q: What are the next steps after using Microsoft Defender for Identity?
A: After deploying Microsoft Defender for Identity, the next steps include setting up and configuring alerts for identity protection, investigating suspicious activities, analyzing threat data, improving the security posture, and reviewing additional resources such as Microsoft Learn.
Q: What is Microsoft Defender for Identity and How Does it Enhance Security Operations?
Microsoft Defender for Identity is a cloud-based security solution designed to help security operations teams protect their organizations from identity-based threats. It uses data from on-premises Active Directory, as well as signals from across Microsoft Defender XDR, to provide identity threat detection. Defender for Identity alerts security teams about suspicious activities and potential security issues involving sensitive users and their group membership. By focusing on identity risk and identity detections, it aims to reduce the attack surface and improve the organization’s overall security posture.
Q: How Does Microsoft Defender for Identity Work with Other Microsoft Security Solutions?
Microsoft Defender for Identity works seamlessly with other Microsoft security solutions like Microsoft Entra and Microsoft 365 portal. It integrates with these platforms to offer a comprehensive view of identity data and security operations. Microsoft Entra, formerly known as Microsoft Azure AD, enhances this integration by providing modern identity and access management solutions. This integration ensures that every user’s identity is protected, whether they are using cloud solutions or on-premises identities managed through Active Directory Certificate Services (AD CS).
Q: What are the Key Features and Capabilities of Microsoft Defender for Identity?
Microsoft Defender for Identity provides several key features and capabilities essential for identity protection. It includes a Defender for Identity workspace within the Microsoft security suite, where security teams can monitor domain controllers and get alerts on identity alerts. The solution uses standalone sensors that can be installed on Windows Server with AD CS to monitor and analyze identity data. These sensors play a crucial role in identifying suspicious activities and reducing the attack surface by focusing on identity risk.
Q: How Do Organizations Set Up and Configure Microsoft Defender for Identity?
Setting up Microsoft Defender for Identity involves installing Microsoft Defender for Identity sensors on Windows Server. The installation might require a reboot of the server. Organizations should ensure that their system meets the software requirements, such as having .NET Framework 4.7 or later and version 1.0 or later of npcap installed with the required settings. There are detailed guides available that describe how to install and configure these components, including steps for silent installation and capacity planning. It’s important to use the installer package that installs npcap OEM and to configure your proxy settings appropriately.
Q: What are the Licensing and Version Requirements for Microsoft Defender for Identity?
To use Microsoft Defender for Identity, organizations must adhere to its licensing model, which is typically part of the broader Microsoft security services. The deployment package for Defender for Identity usually comes with specific version requirements, like the version of npcap (OEM version recommended) and .NET Framework 4.7 or later. Organizations need to ensure they have the correct licensing and that their systems are running the required versions of these software components for optimal functionality and security.
Q: How Does Microsoft Defender for Identity Prioritize Security Alerts and Investigations?
Microsoft Defender for Identity prioritizes security alerts and investigations through its advanced identity threat detection capabilities. It uses data analytics and machine learning to assign investigation priority to different alerts, helping security teams focus on the most critical issues first. The system takes into account various factors, including user profile, behavior patterns, and the nature of the detected activities. This approach helps in effectively managing the workload of security teams and ensures that high-risk incidents are addressed promptly.
Q: What is the Role of Microsoft Secure Score in Enhancing Identity Security with Defender for Identity?
Microsoft Secure Score plays a vital role in enhancing identity security in conjunction with Microsoft Defender for Identity. It provides a quantifiable measure of an organization’s security posture, taking into account various factors like identity alerts, security operations, and the use of Defender for Identity. By following recommendations to improve the Secure Score, organizations can ensure that their identity protection strategies are aligned with best practices, thereby minimizing identity risk and bolstering overall security.
Q: How Does Microsoft Defender for Identity Utilize Standalone Sensors for Enhanced Security?
Microsoft Defender for Identity employs standalone sensors that are installed on Windows Server systems. These sensors are crucial for monitoring and analyzing identity data. They work by examining network traffic and Windows events directly from the server, providing a more thorough understanding of the security landscape. This approach is key in detecting suspicious activities and security issues related to identity. The standalone sensor is a vital component in ensuring the security of identity data and plays a significant role in reducing the attack surface.
Q: What Are the Steps to Configure Microsoft Defender for Identity for Optimal Performance?
Configuring Microsoft Defender for Identity for optimal performance involves several steps. Firstly, the installation of the Microsoft Defender for Identity sensors is crucial. This might require a reboot of the server to ensure the sensors are functioning correctly. Organizations should see the ‘Configure’ section in Microsoft’s documentation for detailed guidance. Additionally, it’s important to ensure that the correct version of npcap is installed. For the best performance, a silent installation of the software is recommended. This helps in capacity planning and ensures that every user and identity in the organization is adequately monitored and protected.
Q: Can You Explain the Importance of Identity-Based Security in Modern Organizations?
Identity-based security is increasingly important in modern organizations due to the evolving nature of cyber threats. Microsoft Defender for Identity focuses on this aspect by providing identity threat detection and identity-based security solutions. By monitoring user profiles and group memberships, it helps in pinpointing potential security breaches that target identities. This is particularly crucial in an environment where both cloud and on-premises systems are in use. By focusing on identities, organizations can better safeguard against unauthorized access and other security risks that specifically target user credentials and access privileges.
Q: What is the Role of Cloud Solution Partners in Implementing Microsoft Defender for Identity?
Cloud Solution Partners play a significant role in implementing Microsoft Defender for Identity in organizations. These partners are well-versed in Microsoft’s security solutions and can provide expert guidance on how to best configure and use Defender for Identity. They assist in integrating the solution with other Microsoft products like Azure AD and Microsoft Entra, ensuring a seamless security experience. Cloud Solution Partners can also help organizations understand and meet the licensing requirements and software prerequisites for Defender for Identity, simplifying the deployment process.
Q: How Does Microsoft Defender for Identity Aid in ITDR and Reducing Identity Risk?
Microsoft Defender for Identity is a key component in IT Disaster Recovery (ITDR) planning, especially concerning identity risk. It provides a robust framework for detecting and responding to identity-based threats, which are a critical aspect of ITDR. By continuously monitoring for suspicious activities and providing timely identity alerts, Defender for Identity helps organizations quickly respond to and mitigate potential identity threats. This proactive approach is essential in reducing the attack surface and protecting against identity compromises that could lead to larger IT disasters.
posture assessments microsoft entra id defender for identity to help