Last Updated on October 17, 2024 by Arnav Sharma
Microsoft announced the availability of Defender for API in Public Preview during the RSA security conference.
What exactly can we accomplish with the Defender for APIs?
- Inventory: You may receive an aggregated view of all managed APIs through a single dashboard.
- Analyze the findings on API security, including information about unauthenticated, underused, or external APIs.
- Reviewing and implementing security suggestions to improve API security posture and harden at-risk surfaces is the first step in improving security posture.
- Classifying APIs that receive or react with sensitive data to facilitate risk prioritisation requires the classification of those APIs.
- Ingest API traffic and monitor it using runtime anomaly detection, machine learning and rule-based analytics, to detect API security threats, including the OWASP API Top 10 most critical threats.
- Integrate with Cloud Security Graph in Defender’s Cloud SecurityPosture Management (CSPM) to provide organization-wide API visibility and risk assessment.
- You can receive API security recommendations and alerts on the Azure API Management interface if the Defender for APIs plan is enabled. This integration is made possible by Azure API Management.
- Integration with Security Information and Event Management (SIEM) Systems: Integrate with security information and event management (SIEM) systems to make it simpler for security teams to investigate existing threat response workflows. Find out more.
Organisations can “gain visibility into business-critical APIs” with the assistance of the new Microsoft Defender for APIs solution that is part of the Microsoft Defender for Cloud service. According to the description of this Microsoft document, Microsoft claims “full lifecycle protection, detection, and response coverage” with Microsoft Defender for APIs.
Inventories of an organization’s managed APIs can be shown as a dashboard, where users can search for “external, unused, or unauthenticated APIs.” A machine learning procedure is used to evaluate the APIs in light of the OWASP Top 10 most dangerous software vulnerabilities. Also, Microsoft Defender for APIs will reveal the APIs accessing confidential data. It makes it possible for organisations to strengthen the configurations that are utilised with the APIs.
Information about Microsoft Defender for APIs is displayed in either the Microsoft Defender for Cloud Portal or the Azure Portal. Microsoft Defender for APIs displays alerts in addition to security recommendations, and it is compatible with a wide variety of security information and event management (SIEM) systems.
APIs enable communications between “users, cloud services and data,” but according to the announcement made by Microsoft, they tend to be “loved by developers and threat actors alike.” APIs are used to enable communications between “users, cloud services and data.”
According to the release, “threat actors are increasingly using APIs as their primary attack vector to breach data from cloud applications,” meaning API security has become a vital concern for chief information security officers (CISOs). It went on to say that conventional security measures based on perimeters are deficient in “API behavioural knowledge, which leaves a big hole in API security.”
An example given by Microsoft is the hack that occurred at the Aussie telecommunicationss company Optus. This hack exposed customer information because “an unprotected and publicly exposed API” did not require user identification for connections.
Microsoft has announced that the preview version of Microsoft Defender for APIs is “now available in most Azure commercial regions.”
Enabling API Protection

API security findings
Examine the inventory as well as the security findings for APIs that have been onboarded using the dashboard for Defender for Cloud API Security. The dashboard provides a breakdown of the number of onboarded devices according to API collections, endpoints, and the services provided by Azure API Management.
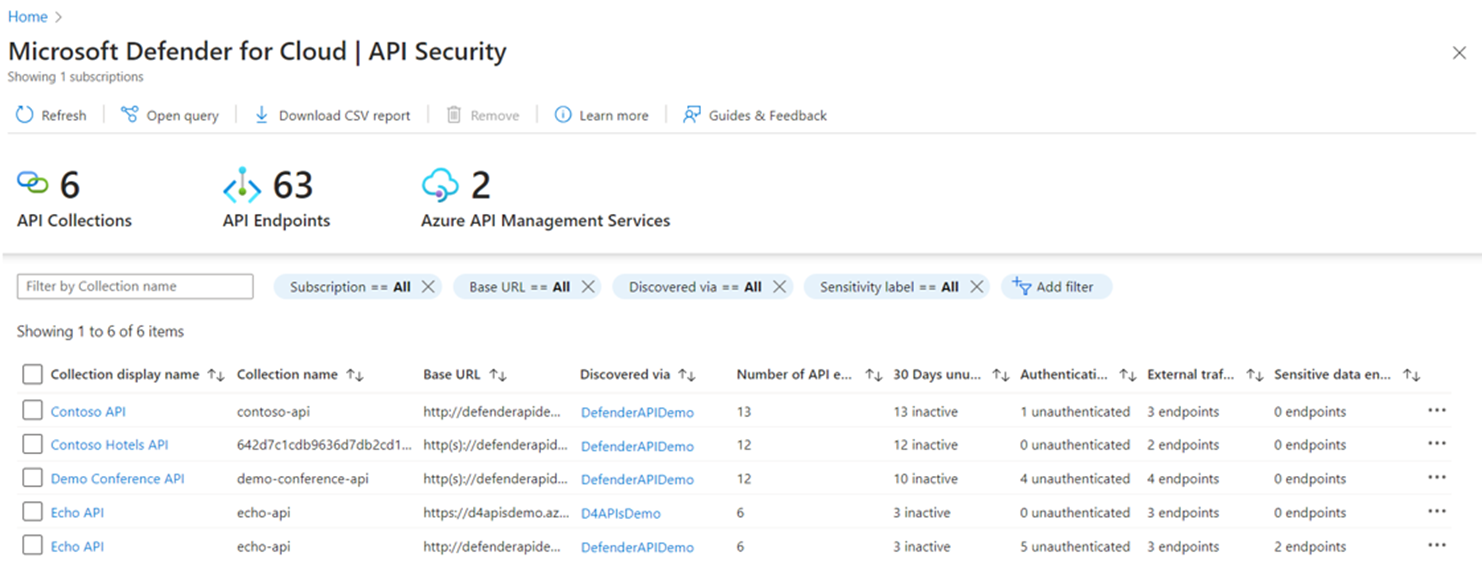
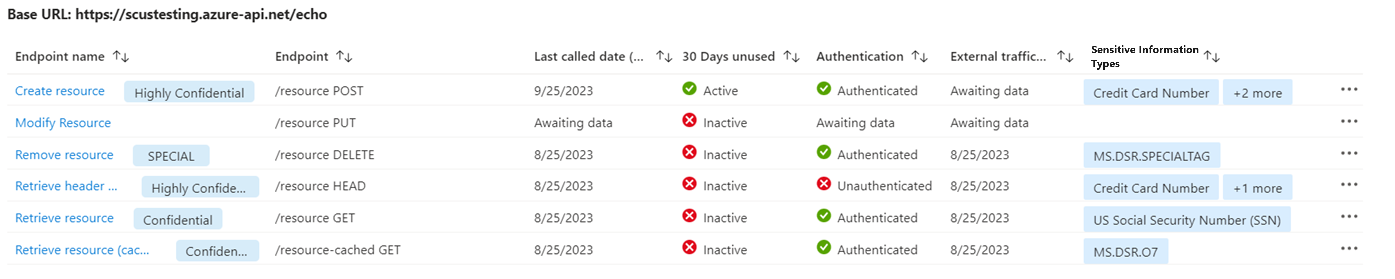
You can drill down into the API collection to review security findings for onboarded API endpoints.
FAQ: Microsoft Defender for APIs in Defender for Cloud
Q: What is Microsoft Defender for APIs?
A: Microsoft Defender for APIs is a cloud-based security solution designed to protect APIs published in Azure API Management services and API endpoints. It provides threat intelligence, anomaly detection, and runtime protection against suspicious API calls and data exfiltration attempts.
Q: How does Defender for APIs provide cloud security?
A: Defender for APIs provides cloud security by monitoring API traffic in real-time and applying machine learning algorithms to detect anomalous behavior. It also integrates with other Microsoft cloud security solutions such as Azure Defender and Microsoft Sentinel to provide a comprehensive security posture for cloud platforms.
Q: What are the key features of Defender for APIs in public preview?
A: Defender for APIs in public preview provides threat intelligence feeds, automatic onboarding of APIs published in Azure API Management services, data classification, security findings for onboarded APIs, and a cloud API security dashboard.
Q: What is Azure Defender and how does it relate to Defender for APIs?
A: Azure Defender is a cloud security posture management (CSPM) solution that provides centralized visibility and control of security for cloud platforms. Defender for APIs can be integrated with Azure Defender to provide advanced security analytics and incident response for APIs published in Azure API Management services.
Q: Can Defender for APIs be integrated with SIEM solutions?
A: Yes, Defender for APIs can be integrated with SIEM solutions using its APIs. It provides a RESTful API and a security events stream for integrating with SIEM solutions such as Microsoft Sentinel.
Q: How can I onboard APIs to Defender for APIs?
A: APIs can be onboarded to Defender for APIs using the Azure API Management portal. APIs published in Azure API Management services can be automatically onboarded to Defender for APIs using its automatic onboarding feature.
Q: What is the Cloud Security Graph and how does it relate to Defender for APIs?
A: The Cloud Security Graph is a centralized security analytics dashboard that provides visibility into security incidents across cloud platforms. Defender for APIs integrates with the Cloud Security Graph to provide security incident response and triage for APIs published in Azure API Management services.
Q: How can I view Defender for Cloud alerts and recommendations?
A: Defender for Cloud alerts and recommendations can be viewed in the Azure Security Center portal. It provides a comprehensive view of security alerts and recommendations for cloud platforms and services.
Q: What is the incident response process for suspicious API calls detected by Defender for APIs?
A: The incident response process for suspicious API calls detected by Defender for APIs involves analyzing the security findings and taking appropriate actions such as blocking the API endpoint, disconnecting the API subscription, or escalating the incident to the security team.
Q: What is data exfiltration and how does Defender for APIs prevent it?
A: Data exfiltration is the unauthorized transfer of data from a protected system. Defender for APIs prevents data exfiltration by monitoring API traffic and applying anomaly detection algorithms to detect suspicious API calls that may indicate data exfiltration attempts.
Q: What are the primary features and capabilities of Microsoft Defender for APIs?
A: Microsoft Defender for APIs provides comprehensive security for APIs, offering features like anomalous and suspicious API activity detection, integration with Defender Cloud Security Posture Management (CSPM), and security insights. It enables the management of APIs within Azure API Management, including onboarding APIs that are exposed using the API management self-hosted gateway. Defender for APIs also integrates with Microsoft Defender for Endpoint, leveraging its capabilities to enhance security coverage.
Q: How does the integration of Defender for APIs with Microsoft Defender for Cloud enhance cloud security?
A: The integration of Defender for APIs with Microsoft Defender for Cloud significantly enhances cloud security. This integration allows for the monitoring and management of your Defender for APIs within the broader cloud security environment. It includes the ability to view the cloud security graph in Defender Cloud Security and leverage the Defender CSPM integration for a more comprehensive understanding of your cloud’s security posture.
Q: Can you explain the process of onboarding APIs to Defender for APIs and its benefits?
A: Onboarding APIs to Defender for APIs involves deploying the Defender for APIs plan within your Azure subscription. This process includes configuring the API management instance in Azure and enabling Defender for APIs. The benefits of onboarding include gaining insights into traffic since onboarding to Defender for APIs, response coverage for APIs, and the ability to detect and manage anomalous and suspicious API activities.
Q: What type of support and resources are available for users of Microsoft Defender for APIs?
A: Users of Microsoft Defender for APIs have access to a range of support and additional resources. This includes technical support for deploying and managing Defender for APIs, access to the Microsoft Security Community for discussions and insights, and educational resources on Microsoft Learn. These resources help users to understand how to use Microsoft Defender effectively and innovate based on its capabilities.
Q: How does Defender for APIs interact with Microsoft Defender for Endpoint and what are the advantages?
A: Defender for APIs interacts with Microsoft Defender for Endpoint by leveraging its set of programmatic APIs and capabilities. This interaction allows Defender for APIs to extend its security measures beyond traditional API management, offering deeper insights and enhanced security measures. The advantage of this interaction is that Defender for Endpoint exposes much more comprehensive data and insights, which can be used to strengthen the security of APIs managed using API Management workspaces.
Q: What is Microsoft Defender for APIs and how does it integrate with other Microsoft Defender services?
A: Microsoft Defender for APIs provides a comprehensive solution for securing APIs within the Microsoft ecosystem. It integrates seamlessly with various Microsoft Defender services, such as Defender for Endpoint and Defender CSPM (Cloud Security Posture Management), enhancing cloud security. This integration allows for advanced API security insights and the ability to automate workflows, leveraging the robust capabilities of Microsoft Defender for Endpoint.
Q: How does Defender for APIs work with Azure API Management?
A: Defender for APIs is enabled to work in conjunction with Azure API Management, allowing for enhanced management of APIs. This collaboration ensures that APIs deployed through Azure API Management are secured and monitored, providing an additional layer of security for APIs within the Azure management instance.
Q: Can Defender for APIs onboard APIs that are not initially included?
A: While Defender for APIs currently doesn’t onboard APIs that are not initially included, it is designed to manage and secure a wide range of APIs. This means that users can innovate and onboard APIs that are exposed through other channels, thereby extending the security coverage provided by Defender for APIs.
Q: What are the deployment and management features of Defender for APIs?
A: Defender for APIs deployment is straightforward, integrating directly into the Microsoft security ecosystem. Users can manage their Defender for APIs plan through the Cloud Security Explorer, which provides additional resources and insights. The deployment process ensures that APIs from Defender for APIs are effectively monitored and secured.
Q: How does Defender for APIs enhance API security?
A: Defender for APIs helps you to gain detailed insights into your API security posture. By providing API security insights and integrating with Defender CSPM, it enables organizations to better manage and protect their APIs. This includes receiving alerts and insights on potential threats, thereby increasing the overall security of the APIs.
Q: What potential benefits can organizations expect from using Defender for APIs?
A: Organizations using Defender for APIs may experience an increase in their overall security posture, especially regarding their API infrastructure. The integration with Microsoft Defender for Endpoint and other APIs within the Defender suite enhances the capability to detect and respond to threats, offering a more robust security solution.
Q: Can Defender for APIs assist in automating security workflows?
A: Yes, Defender for APIs can be used to automate workflows related to API security. This feature allows for a more efficient management of security protocols and responses, reducing manual effort and improving response times to potential security incidents.
Q: Is there a way to learn more about deploying and using Defender for APIs?
A: To learn more about deploying and managing Defender for APIs, you can utilize additional resources such as the Cloud Security Explorer and Microsoft’s own documentation. These resources provide valuable insights into how you can use Defender for APIs to enhance your organization’s security.
