Last Updated on October 29, 2024 by Arnav Sharma
In the previous blog, we explored the foundational concepts of Microsoft Copilot for Security, including what it is, how it leverages generative AI, and the core principles behind its powerful capabilities. We discussed how Copilot acts as an AI-driven assistant to security teams, automating complex tasks and providing valuable insights through natural language processing. Building on that understanding, this blog will dive deeper into the key use cases and practical features of Microsoft Copilot for Security. We’ll also look at how it integrates into existing security workflows, enabling organizations to enhance their cybersecurity operations effectively.
A Quick Recap: What is Microsoft Copilot for Security?
Microsoft Copilot for Security is an AI-powered, cloud-based tool designed to assist security analysts by automating key security tasks, summarizing incidents, and enhancing decision-making. It leverages large language models (LLMs) to process data at machine speed, making it possible to respond to threats faster and with greater precision. But beyond this foundational understanding, let’s delve into how Copilot can be applied in real-world scenarios and the practical value it offers.
Key Use Cases of Microsoft Copilot for Security
Microsoft Copilot for Security is not just a reactive tool—it’s a proactive assistant that empowers security professionals to streamline operations and enhance threat response. Here are some of the key use cases where Copilot excels:
1. Incident Summarization
When security incidents occur, analysts are often bombarded with a sea of alerts and signals. Copilot for Security uses generative AI to distill this overwhelming data into concise, actionable summaries. By automatically summarizing complex alerts, Copilot helps analysts quickly understand incidents, their impact, and the necessary next steps. This feature is especially valuable for incident response teams that need clear, actionable information to communicate effectively and coordinate their actions.
2. Impact Analysis
One of the most critical aspects of incident response is understanding the broader impact of a security event. Copilot’s AI-driven analytics can assess the potential consequences of an incident, including the systems affected, the severity of the breach, and the overall risk to the organization. This insight allows analysts to prioritize their response efforts and focus on the most critical areas, reducing overall risk and improving the efficiency of their operations.
3. Reverse Engineering of Scripts
Cybersecurity analysts often encounter suspicious or malicious scripts, which can be challenging to analyze manually. Copilot for Security includes a reverse engineering capability that can analyze complex command-line scripts and automatically translate them into plain language. This feature not only saves time but also eliminates the need for deep technical expertise to understand malicious code. By making reverse engineering more accessible, Copilot democratizes this critical task and allows analysts to focus on mitigation.
4. Guided Responses
Incident response can be a chaotic and high-pressure process, with analysts needing clear and actionable guidance to respond effectively. Copilot for Security provides step-by-step instructions for incident response, including triage, investigation, containment, and remediation. These guided responses are tailored to the specific incident, offering detailed actions and deep links to relevant resources. This structured approach improves response times and ensures that critical steps are not overlooked.
Standalone and Embedded Experiences
One of the standout features of Microsoft Copilot for Security is its flexibility in deployment. Copilot can be accessed in two main configurations: as a standalone experience or as an embedded experience within existing Microsoft products.
Standalone Experience
In the standalone experience, Copilot is accessed through a dedicated portal. This mode allows users to interact directly with the tool by entering natural language prompts. The dedicated interface is designed to be intuitive and user-friendly, enabling analysts to quickly obtain insights and take action. For example, an analyst might use the standalone Copilot experience to request a summary of incidents or an impact analysis, and the AI-powered assistant will generate a detailed response.
The standalone experience is ideal for security teams looking to leverage Copilot’s full capabilities in a focused environment. Analysts can access a broad range of features, including plugins and custom promptbooks, which allow for tailored security analyses and streamlined workflows.
Embedded Experience
The embedded experience is designed to integrate Copilot’s capabilities directly into other Microsoft security products. For instance, security analysts working within Microsoft Sentinel or Microsoft Defender can access Copilot’s insights without leaving their primary workspace. This seamless integration enables analysts to conduct investigations, respond to incidents, and perform in-depth analyses without the need to switch between different platforms.
By embedding Copilot’s capabilities within existing tools, Microsoft has created a unified experience that enhances productivity and efficiency. Security analysts can now access contextual assistance and AI-generated insights within the applications they use every day, reducing friction and improving response times.
Extending Copilot Capabilities: Plugins and Promptbooks
To extend its functionality, Microsoft Copilot for Security leverages plugins and promptbooks. Let’s explore these in more detail:
Plugins
Plugins are collections of capabilities that allow Copilot to interact with various data sources and security tools. For example, Copilot can integrate with Microsoft Sentinel, Microsoft Defender, and Microsoft Intune through specific plugins. These plugins provide specialized functions, such as generating incident reports, analyzing files, and summarizing the security state of a device. By connecting with different tools, Copilot can provide comprehensive insights that span multiple security domains.
Promptbooks
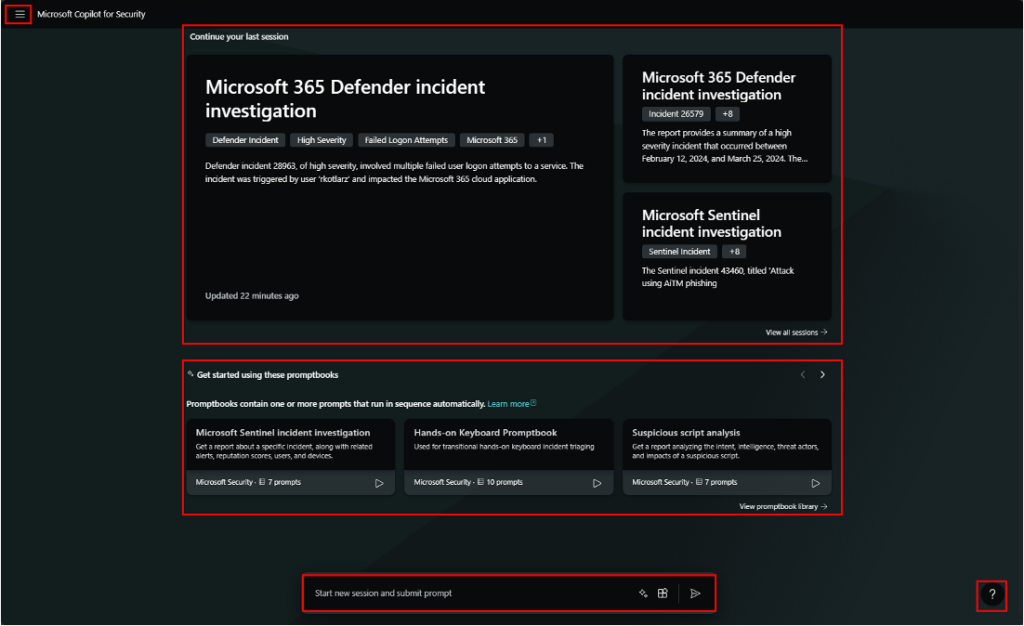
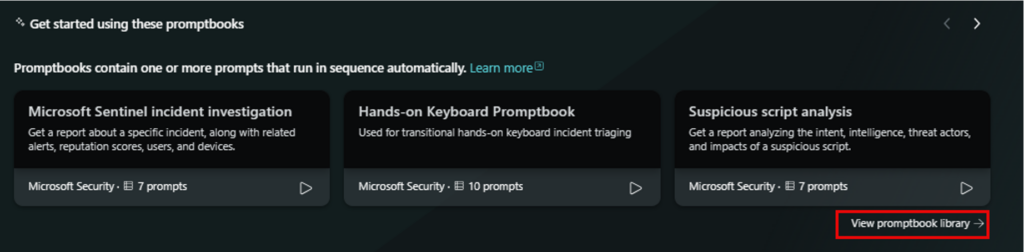
Promptbooks are collections of pre-defined prompts designed to accomplish specific security-related tasks. These promptbooks serve as templates that analysts can use to quickly generate responses and insights. For instance, a promptbook might contain a set of prompts for investigating phishing incidents, analyzing malware, or assessing vulnerabilities. By using promptbooks, security teams can standardize their workflows and ensure consistent analysis across different incidents.
Key Terminology and Concepts
Understanding the terminology used in Microsoft Copilot for Security is essential for effectively leveraging its capabilities. Here are some key terms to familiarize yourself with:
- Session: A session refers to a particular conversation or interaction within Copilot. It maintains context and continuity throughout the interaction.
- Prompt: A specific user statement or question within a session. Prompts are entered into the prompt bar to request insights from Copilot.
- Capability: A function that Copilot uses to solve part of a problem. Capabilities are often linked to specific plugins and data sources.
- Plugin: A collection of capabilities provided by a particular data source or tool, such as Microsoft Sentinel or Microsoft Defender.
- Orchestrator: The system responsible for composing capabilities together to answer a user’s prompt.
Crafting Effective Prompts for Copilot
One of the most crucial elements of using Microsoft Copilot effectively is understanding how to craft prompts. The quality of the prompts you provide directly influences the quality of the responses you receive. When crafting prompts, security analysts should focus on the following elements:
- Goal: Clearly define the specific security-related information you need. Be explicit about what you are asking Copilot to do.
- Context: Provide context for why you need the information or how you plan to use it. This helps Copilot generate more relevant and accurate responses.
- Expectations: Specify the format or the target audience for the response. This ensures the output aligns with your needs.
- Source: Indicate any known data sources or plugins that should be used to gather information.
For example, if you are investigating a security incident involving a particular malware strain, you might craft a prompt like: “Summarize all known indicators of compromise and TTPs (tools, tactics, and procedures) for the Conti ransomware.” This prompt clearly defines the goal, context, and expectations for the response, enabling Copilot to provide a detailed and actionable output.
Conclusion
Microsoft Copilot for Security offers a wealth of features and capabilities that empower security professionals to work more efficiently and effectively. From incident summarization and impact analysis to reverse engineering scripts and providing guided responses, Copilot transforms how organizations handle cybersecurity challenges. By offering both standalone and embedded experiences, Copilot provides flexibility in deployment and seamlessly integrates with existing security tools.
In our next blog, we’ll explore how to set up Microsoft Copilot for Security in your organization, including provisioning capacity, configuring environments, and assigning roles. Stay tuned to learn more about getting started with Copilot and optimizing its deployment!
FAQ:
Q: What is Microsoft 365 and how is it used in security operations?
A: Microsoft 365 is a comprehensive suite of productivity and collaboration tools, including apps like Microsoft Teams, integrated with security and compliance features across Microsoft products. It is used extensively to enhance security operations by providing capabilities such as Microsoft Defender XDR and Microsoft Defender for Endpoint, ensuring data security and compliance within the organization.
Q: How does Microsoft 365 Copilot help with security?
A: Copilot for Microsoft 365 integrates with Microsoft Defender products and other security tools, providing an assistive Copilot experience that helps security and IT teams handle complex security alerts. It uses AI-powered security analysis tools to generate concise, actionable insights from large volumes of security data and signals across different Microsoft security solutions.
Q: What is Microsoft Security Copilot and what does it offer?
A: Microsoft Security Copilot is an AI-powered cybersecurity product designed to enhance security professionals’ response capabilities. It integrates with products like Microsoft Defender Threat Intelligence, providing direct access to Microsoft’s security experts and analysis tools. This embedded experience helps professionals manage security incidents efficiently by transforming complex security alerts into concise insights.
Q: What is Microsoft Purview, and how does it contribute to data security?
A: Microsoft Purview is a comprehensive solution that enables organizations to manage and protect their data across the cloud and on-premises environments. It offers data security and compliance features that help organizations maintain visibility into their data and enforce security best practices, ensuring data protection at all levels.
Q: How does Microsoft use AI to strengthen its security portfolio?
A: Microsoft utilizes AI-powered security solutions to enhance visibility into security threats, streamline security alerts, and automate responses to emerging risks. AI-driven tools like Microsoft Security Copilot enable organizations to leverage advanced security capabilities within the Microsoft security portfolio, such as Microsoft Defender External Attack Surface Management and Microsoft Defender for Endpoint.
Q: How can Microsoft Security Copilot support security training?
A: Microsoft Security Copilot not only assists with real-time threat management but also helps security professionals gain insights into common security issues and best practices. It offers an embedded experience that supports learning within the context of daily security operations, making it a valuable resource for ongoing security training and upskilling within teams.
Q: What kind of visibility does Microsoft Entra offer in terms of security and compliance?
A: Microsoft Entra provides comprehensive visibility into security and compliance by managing access to organizational data and resources. It enables organizations to enforce security policies and controls across users and applications, ensuring that only authorized individuals have the appropriate level of access to critical information.
