Last Updated on May 30, 2024 by Arnav Sharma
A social engineering attack is a technique used by cybercriminals to manipulate and deceive individuals into divulging confidential information or performing actions that may compromise their security. These attacks exploit human psychology and involve the manipulation of trust to gain unauthorized access to sensitive data or systems, underlining the critical role of social engineering in cybersecurity.
What is a social engineering attack?
Definition of social engineering attack
A social engineering attack is a form of cyber attack in which threat actors use psychological manipulation to deceive individuals into disclosing confidential information, providing access to protected systems, or performing actions that may compromise security.
Types of social engineering attacks
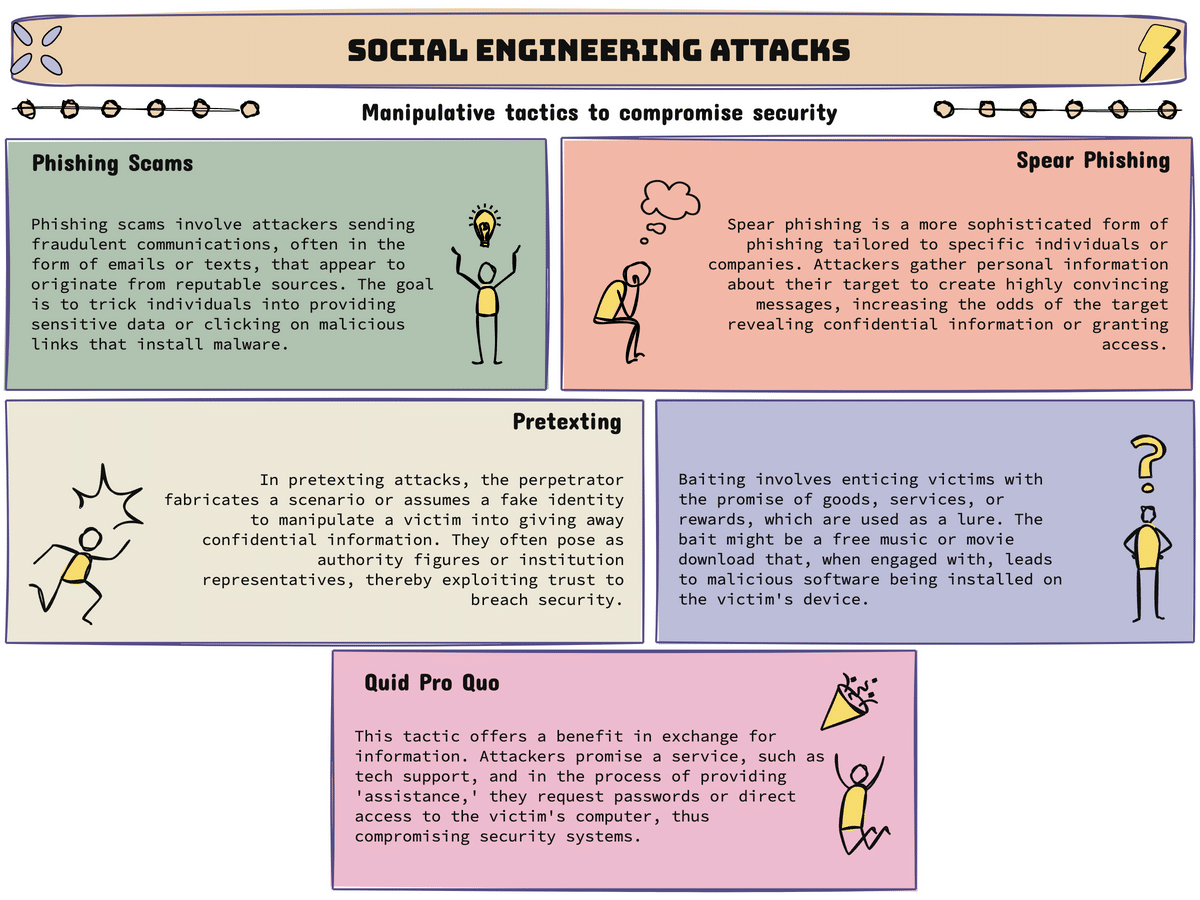
There are various types of social engineering attacks, each aiming to exploit different aspects of human behavior and interaction. Some common types of social engineering attacks include phishing scams, pretexting, baiting, quid pro quo, and tailgating.
Examples of social engineering attacks
Here are five examples of social engineering attacks that have been used by cybercriminals, highlighting the diversity of attack types in cybersecurity.
- Phishing scams: In a phishing attack, attackers send fraudulent emails or text messages posing as trusted entities, such as banks or online services, to trick users into revealing their login credentials or other sensitive information.
- Spear phishing attacks: Spear phishing attacks are more targeted and personalized, where the attacker carefully researches their victims to craft tailored messages that appear legitimate and trustworthy.
- Pretexting: Pretexting involves creating a false scenario, such as impersonating a colleague or a technical support representative, to manipulate individuals into revealing sensitive information or performing actions that benefit the attacker.
- Baiting: Baiting attacks involve enticing individuals with an offer or reward, such as a free USB drive or access to exclusive content, to make them unknowingly download malware or compromise their security in some way.
- Quid pro quo: In a quid pro quo attack, attackers promise a benefit or service in exchange for the disclosure of confidential information or access to a protected system.
How to prevent social engineering attacks?
Security awareness training
One of the most effective ways to prevent social engineering attacks is through security awareness training. By educating individuals about the techniques and tactics used by social engineers, they become more cautious and better equipped to identify and report suspicious activities.
Using security software
Having up-to-date security software, such as antivirus and anti-malware programs, can help detect and prevent social engineering attacks. These tools can identify and block malicious websites, emails, and attachments that may contain malware.
Recognizing phishing emails
Being able to recognize and identify phishing emails is crucial in preventing falling victim to social engineering attacks. Users should pay attention to suspicious email addresses, grammar and spelling errors, and requests for personal or financial information.
What are some examples of social engineering techniques?
Phishing scams
Phishing scams are one of the most common social engineering techniques used by cybercriminals. In these attacks, individuals receive deceptive emails or messages designed to trick them into disclosing sensitive information, such as login credentials or credit card details.
Spear phishing attacks
Spear phishing attacks are similar to phishing scams but are more targeted. Attackers research their victims and personalize their messages to increase the likelihood of success, often seeking information like social security numbers or the date of birth to bypass security measures. These attacks often appear as legitimate requests from colleagues, business partners, or trusted organizations.
Pretexting
Pretexting involves creating a fictional scenario or pretext to manipulate individuals into sharing confidential information or performing actions that compromise their security, illustrating a complex form of social engineering in cybersecurity. This technique often involves impersonating authoritative figures or technical support personnel, a classic example of social engineering in cybersecurity.
How do attackers use social engineering?
Impersonating trusted individuals
One way attackers use social engineering is by impersonating trusted individuals or entities. They may pose as a colleague, friend, or technical support representative to gain the trust and cooperation of their targets.
Exploiting vulnerabilities
Social engineers exploit human vulnerabilities, such as the desire for convenience or the fear of missing out, to trick individuals into taking actions that may compromise their security. By exploiting these weaknesses, attackers can manipulate their targets into revealing sensitive information or downloading malicious software.
Tricking users to reveal login credentials
Social engineers often trick users into divulging their login credentials through various deceptive tactics. This could involve creating fake login pages or sending phishing emails that mimic legitimate websites or services.
What are the consequences of falling victim to social engineering attacks?
Potential loss of sensitive information
Falling victim to social engineering attacks can result in the loss of sensitive personal or corporate information. Attackers may gain access to financial data, login credentials, or other confidential information, which can lead to financial loss or identity theft.
Infection of systems with malware
Social engineering attacks often involve the distribution of malware, which can infect systems and cause significant damage. Malicious software can compromise data, disrupt operations, and even give attackers remote control over infected devices.
Business email compromise
Business email compromise (BEC) is a type of social engineering attack that targets organizations. Attackers impersonate executives or other trusted employees and manipulate employees into transferring money or sensitive information to fraudulent accounts, showcasing a form of social engineering in cybersecurity.
FAQ:
Q: What is social engineering?
A: Social engineering is the art of manipulating individuals to gain unauthorized access to information or systems. It relies on exploiting human psychology and tricking people into providing sensitive information or performing actions that they wouldn’t under normal circumstances.
Q: What are the different types of social engineering attacks?
A: Some of the most common types of social engineering attacks include phishing, spear phishing, scam, pretexting, and baiting. Each type targets victims in different ways, but they all aim to deceive and manipulate people into giving up personal or confidential information.
Q: What is phishing?
A: Phishing is a type of social engineering attack where cybercriminals send fraudulent emails or messages, disguising themselves as a trustworthy source, in order to trick individuals into revealing sensitive information or downloading malware onto their devices.
Q: Can you provide some examples of social engineering attack?
A: Sure! Here are five examples of social engineering attacks in cybersecurity: 1) An attacker posing as a bank representative calls a victim and convinces them to reveal their online banking credentials. 2) A scammer sends an email pretending to be from a popular social media platform, asking the recipient to click on a link to verify their account. 3) An unsuspecting employee receives a phone call from someone pretending to be from IT support, requesting their login credentials to fix a supposed email account issue, demonstrating the importance of adhering to security policies in the workplace. 4) A hacker sends a phishing email claiming to be from a trusted online retailer, asking the recipient to provide their credit card information to complete a purchase, a tactic that stresses the necessity for robust cybersecurity measures. 5) A cybercriminal creates a spoofed website that looks like a legitimate bank login page, tricking users into entering their passwords, which are then stolen.
Q: How can I defend against social engineering attacks?
A: To defend against social engineering attacks, it’s important to: 1) Be cautious of unexpected or unsolicited communications, especially those that create a sense of urgency or ask for sensitive information. 2) Verify the identity of individuals or organizations before providing any personal or financial information. 3) Regularly update and use strong, unique passwords for all online accounts, a key prevention tip to safeguard against various forms of social engineering in cybersecurity. 4) Install and keep software and operating systems up to date to prevent vulnerabilities that attackers may exploit, abiding by key prevention tips in cybersecurity. 5) Educate yourself and your employees about social engineering tactics and common scams to recognize and avoid them.
Q: How can I protect against social engineering attacks on popular social networks?
A: To protect yourself against social engineering attacks on popular social networks, you can: 1) Enable two-factor authentication to add an extra layer of security to your accounts. 2) Be cautious of friend requests or messages from unfamiliar individuals, especially if they ask for personal or financial information. 3) Avoid clicking on suspicious links or downloading files from unknown sources. 4) Regularly review your privacy settings to limit the amount of personal information that is publicly accessible. 5) Report any suspicious or abusive behavior to the social networking platform.
Q: What is the role of cyber security in defending against social engineering attacks?
A: Cyber security plays a crucial role in defending against social engineering attacks. By implementing strong security measures, such as firewalls, intrusion detection systems, and advanced email filtering, organizations can prevent and detect social engineering threats. Additionally, promoting cyber security awareness and training employees to recognize and respond to social engineering attacks can significantly reduce the risk.
Q: What can happen if I fall victim to a social engineering attack?
A: If you fall victim to a social engineering attack in cybersecurity, the consequences can be severe. Attackers can gain access to your personal data, financial accounts, and even your email account. They may use this information to commit identity theft, make unauthorized transactions, or carry out further attacks. It’s important to act quickly if you suspect you’ve been targeted or compromised, and report the incident to your security team immediately.
Q: What are some popular social engineering attacks that people should be aware of?
A: Some popular social engineering attacks that people should be aware of include phishing scams, rogue security software, and impersonation scams. These scams often rely on creating a sense of urgency or fear to trick individuals into taking immediate action or revealing sensitive information, epitomizing a prevalent attack type in the realm of cybersecurity. Staying informed about the latest social engineering attack techniques can help you stay vigilant and better protect yourself.
Q: How can I secure my email against social engineering attacks?
A: To secure your email against social engineering attacks, you can: 1) Use a strong, unique password for your email account. 2) Enable two-factor authentication for an extra layer of security. 3) Be cautious of emails that ask for sensitive information or contain suspicious links or attachments. 4) Regularly update your email software and keep your operating system patched. 5) Be wary of emails that create a sense of urgency or ask you to take immediate action.
Q: What are the key elements of a successful social engineering attack?
A: A successful social engineering attack often relies on several key elements: 1) Establishing trust or credibility with the victim. 2) Exploiting the victim’s emotions, such as fear or curiosity. 3) Creating a sense of urgency or importance. 4) Providing a plausible pretext or reason for the victim to take the desired action. 5) Manipulating the victim into providing sensitive information or performing an action that benefits the attacker. By understanding these elements, you can better protect yourself against social engineering attacks through effective cybersecurity measures.
Q: What does social engineering work involve?
A: Social engineering work involves the use of social engineering techniques to manipulate individuals into giving away sensitive information.
Q: What is bait in the context of social engineering?
A: Bait in the context of social engineering can refer to a type of phishing attack where attackers use enticing offers to lure victims into giving away sensitive information.
Q: How does quid pro quo function in social engineering attacks?
A: Quid pro quo in social engineering attacks involves attackers offering something desirable in exchange for information or access.
Q: What are common attack techniques in social engineering?
A: Common attack techniques in social engineering include phishing campaigns, voice phishing, angler phishing, and whaling attacks.
Q: What is the social engineering definition?
A: Social engineering refers to the psychological manipulation of people into performing actions or divulging confidential information.
Q: How can one identify social engineering attacks?
A: One can identify social engineering attacks by recognizing common tactics such as phishing emails, fake social media accounts, and suspicious requests for sensitive information.
Q: How can one mitigate the risk of social engineering?
A: To mitigate the risk of social engineering, one can use prevention methods such as internet security software, a security strategy, and physical security measures.
Q: What is the risk of social engineering?
A: The risk of social engineering is that it can lead to cybersecurity attacks where attackers manipulate individuals to give away sensitive information, potentially compromising information security.