Last Updated on August 12, 2024 by Arnav Sharma
In today’s digital world, the threat of cyber attacks is ever-present. Organizations must be prepared to respond effectively to any security incident to protect their assets and maintain trust. This is where a robust cyber incident response plan comes into play. Here, we’ll explore the 6 phases in an effective incident response plan, detailing each phase and its importance in the overall cybersecurity strategy.
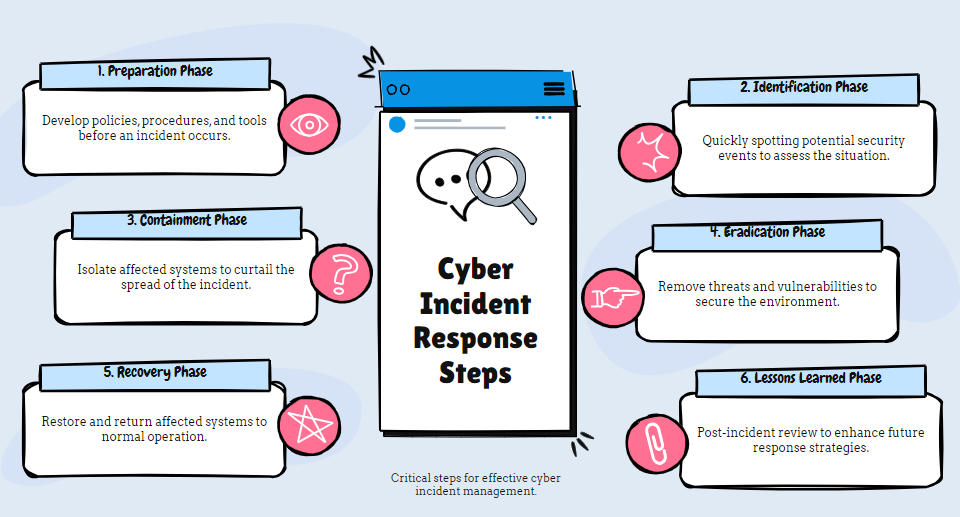
1. Preparation Phase: Laying the Foundation for Incident Response
The preparation phase of the incident response plan is crucial for establishing an effective incident response capability. During this phase, organizations develop policies, procedures, and a communication plan. Key activities include:
- Incident Response Team: Forming a dedicated incident response team, often referred to as a computer security incident response team (CSIRT), which is responsible for handling and managing security incidents. This team should include skilled professionals from various departments who can work together seamlessly during a cyber crisis.
- Security Tools: Deploying necessary security tools and technologies to detect and respond to incidents. This includes intrusion detection systems (IDS), security information and event management (SIEM) systems, and other monitoring tools that help in identifying and mitigating cyber threats.
- Training: Conducting regular training and awareness programs for employees and incident responders. This ensures everyone knows how to recognize signs of an incident and the steps to take when a security event occurs. Training should cover various types of incidents and the appropriate response strategies.
- Response Plan Template: Creating an incident response plan template to guide actions during an incident. This template should outline the incident response steps, including immediate response actions, communication protocols, and documentation requirements. It serves as a comprehensive response plan to ensure consistency and efficiency in handling incidents.
A well-prepared organization can swiftly and efficiently handle any computer security incident that arises.
2. Identification Phase: Detecting and Recognizing Cyber Threats
The identification phase focuses on detecting and identifying potential security incidents. This phase involves:
- Signs of an Incident: Monitoring systems for unusual activity and signs of an incident. This includes unusual network traffic, unauthorized access attempts, and other indicators of a possible cyber attack.
- Security Incident Handling: Analyzing alerts and logs to validate incidents. This involves using automated tools and manual analysis to determine if a security event is a real incident or a false positive.
- Incident Documentation: Ensuring complete documentation of the incident for future reference. Documenting every step taken throughout the process helps in understanding the incident better and aids in post-incident analysis.
An effective incident response plan is essential for quickly recognizing and validating threats, minimizing potential damage.
3. Containment Phase: Controlling the Incident to Prevent Further Damage
Once a security incident is confirmed, the containment phase aims to limit its impact. Key steps include:
- Immediate Response: Implementing short-term and long-term containment strategies. Short-term containment involves actions like isolating affected systems, while long-term containment focuses on more sustainable measures to prevent further damage.
- Affected Systems: Isolating affected systems to prevent the spread of malicious activity. This may involve disconnecting infected devices from the network or shutting down compromised services temporarily.
- Incident Handlers: Utilizing incident handlers to execute containment measures. These are the individuals responsible for carrying out the containment phase of the cyber incident response plan, ensuring that all actions are performed effectively and efficiently.
The containment phase is critical to ensure the cyber attack does not cause widespread harm.
4. Eradication Phase: Eliminating the Root Cause
The eradication phase focuses on removing the root cause of the incident and ensuring that the environment is clean. Activities include:
- Root Cause: Identifying and addressing the root cause of the incident. This involves understanding how the breach occurred and what vulnerabilities were exploited.
- Malicious Components: Removing malware and any other malicious components. This includes cleaning up infected systems, deleting malicious files, and ensuring no remnants of the attack remain.
- Mitigate Risks: Closing vulnerabilities to prevent similar attacks in the future. This may involve applying patches, updating software, changing configurations, and enhancing security controls to strengthen the organization’s defenses.
A thorough eradication phase ensures that the systems are safe and secure before moving to the next steps.
5. Recovery Phase: Restoring Normal Operations
After the eradication, the recovery phase aims to bring systems back online carefully. Key activities include:
- Systems Back Online: Restoring affected systems and services. This involves rebuilding systems from clean backups, ensuring data integrity, and verifying that all services are functioning correctly.
- Monitoring: Keeping a close eye on systems to detect any residual threats. Continuous monitoring helps in identifying any lingering issues that may not have been addressed during eradication.
- Validation: Ensuring that all systems are fully functional and secure. Conducting thorough testing to validate that the incident has been fully resolved and that systems are operating normally.
The recovery phase is vital to resume normal operations while ensuring that the threat has been completely neutralized.
6. Lessons Learned Phase: Analyzing and Improving
The final phase, lessons learned, focuses on reviewing the incident and improving future responses. Activities include:
- Incident Review: Conducting a thorough post-incident review. This involves analyzing the incident response process, identifying what went well and what could be improved.
- Lessons Learned: Documenting what happened, how it was handled, and what could be improved. This documentation helps in refining the incident response plan and preparing for future incidents.
- Incident Response Process: Updating the incident response process based on insights gained. Making necessary changes to policies, procedures, and tools to enhance the organization’s cyber incident response capabilities.
- Effective Response: Sharing lessons learned with the incident response team and relevant stakeholders. This ensures that everyone is aware of the improvements and that similar attacks can be handled more effectively in the future.
This phase ensures continuous improvement in the organization’s incident response capabilities, making them better prepared for future cyber security incidents.
FAQ:
Q: What is an incident response plan?
An incident response plan is a comprehensive response plan that outlines steps and procedures to handle cybersecurity incidents effectively.
Q: What are the 6 phases of incident response?
The 6 phases of incident response are preparation, identification, containment, eradication, recovery, and lessons learned. These phases in the incident response process ensure a thorough approach to managing incidents.
Q: What is the SAN incident response framework?
The SAN incident response framework is a guideline for creating an effective incident response plan, incorporating phases of incident response to handle cybersecurity incidents.
Q: Who makes up a cyber incident response team?
An incident response team, or cyber incident response team, includes IT professionals, security analysts, legal advisors, and communication experts. Their role is critical in executing the incident response plan.
Q: What is a cyber incident response process?
A cyber incident response involves a set of steps to address, manage, and mitigate the impact of a cybersecurity incident, such as a data breach or other security threats.
Q: What constitutes a data breach in cyber security?
A breach, or data breach, refers to the unauthorized access, disclosure, or theft of sensitive information, requiring immediate and effective incident response.
Q: What should a cyber incident response plan include?
A cyber incident response plan should include detailed incident response steps, roles and responsibilities, communication strategies, and procedures for each phase of incident response.
Q: What is the response process in incident response?
The response process involves detecting the incident, assessing its impact, containing the threat, eradicating the cause, recovering systems, and conducting a post-incident review to improve future responses.
Q: Why is cybersecurity important?
Cybersecurity is crucial to protect sensitive information, ensure data integrity, and maintain system availability. An effective cyber incident response plan is vital in managing incidents.
Q: What are the key components of an effective incident response plan?
An effective incident response includes a well-defined plan, a trained response team, clear communication channels, and regular testing and updating of the plan. These components help manage incidents like a data breach.
Q: What is a cybersecurity incident?
A cybersecurity incident is an event that compromises the confidentiality, integrity, or availability of information systems and data, triggering the incident response process.
Q: What is the purpose of each phase of incident response?
Each phase of incident response serves a specific purpose: preparation sets the groundwork, identification detects incidents, containment limits damage, eradication removes threats, recovery restores systems, and lessons learned improve future responses.