Last Updated on June 23, 2024 by Arnav Sharma
Overview of HashiCorp Boundary
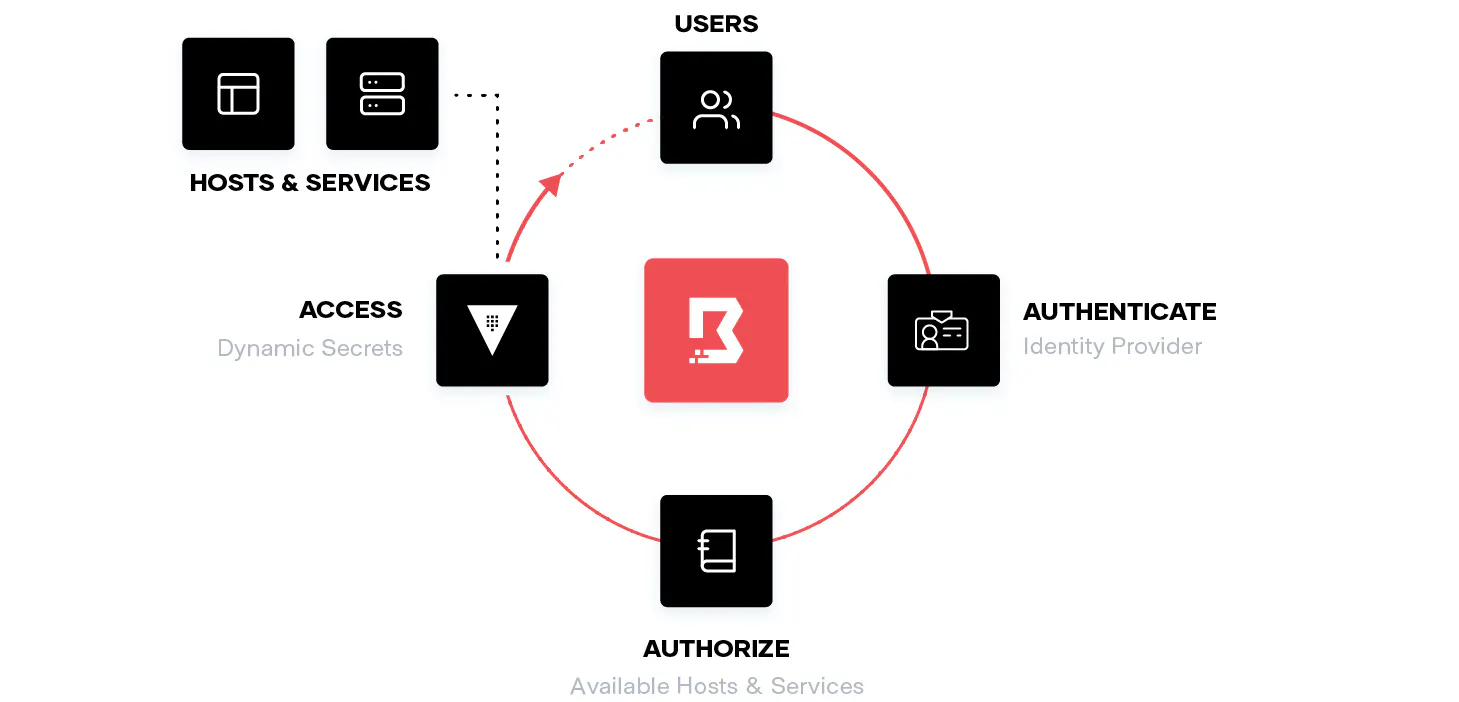
HashiCorp Boundary is a secure remote access solution designed to provide simple and secure access to dynamic infrastructure across various environments. Unlike traditional SSH bastion hosts, Boundary allows you to manage access to applications and critical systems without exposing the underlying network, offering a more secure and efficient way to handle remote user access.
Key Features of HashiCorp Boundary
Identity-Based Access Control
HashiCorp Boundary provides a secure way to access hosts and critical systems through just-in-time access and role-based access controls. This ensures that access to sensitive systems is tightly controlled and monitored, reducing the risk of unauthorized access.
Integration with HashiCorp Vault
By integrating with HashiCorp Vault, Boundary enhances credential management. Vault securely stores and manages secrets, providing dynamic credentials for accessing critical systems, which Boundary uses to authenticate and authorize access based on trusted identities.
Dynamic Host Catalogs
Boundary’s dynamic host catalogs automatically discover and catalog new resources, simplifying access management and ensuring that access policies are always current.

Enhancing User Access
Streamlined User Access
Boundary streamlines user access to dynamic infrastructure by leveraging identity-based access controls. This ensures that users can securely access the systems they need, without exposing the network to potential threats.
Multi-Cloud Support
Boundary can be deployed across multiple cloud environments, including AWS and Azure, providing a consistent and secure access management solution for infrastructure hosted on different platforms.
Automation and Credential Management
Credential Management
With Boundary, credentials are dynamically managed and injected when needed, reducing the need for static credential distribution and management. This approach enhances security and simplifies credential management.
Automation with Terraform
Boundary’s Terraform provider allows you to define access control policies as code, making it easy to automate and manage access configurations.
Secure Remote Access
Secure Access to Critical Systems
Boundary is a remote access solution that provides secure access to applications and critical systems. It ensures that remote user access is managed efficiently, with fine-grained authorizations based on trusted identities.
Authentication and Authorization
Boundary uses identity providers like Okta and Azure Active Directory to authenticate users, ensuring that only authorized individuals can access sensitive systems.
Session Management and Recording
Session Recording and Audit
Boundary’s session recording and audit features provide comprehensive visibility into user activities, enhancing security and compliance by allowing you to track and review access to critical systems.
Step-by-Step Guide
1. Install Boundary CLI
First, download and install the Boundary CLI from the official HashiCorp website. Below are the installation commands for different operating systems.
For Debian-based Linux (Ubuntu):
curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
sudo apt-get update && sudo apt-get install boundary
For macOS using Homebrew:
brew tap hashicorp/tap brew install hashicorp/tap/boundary
For Windows using Chocolatey:
choco install boundary
2. Initialize Boundary
Initialize a development environment to start exploring Boundary features.
Command:
boundary dev
This command starts a local development instance of Boundary for testing and learning purposes.
3. Configure Authentication
Set up your authentication method. For example, to configure OIDC with Okta:
Command:
boundary auth-methods create oidc -name "okta" -url "https://your-okta-domain.okta.com" -client-id "your-client-id" -client-secret "your-client-secret"
Replace your-okta-domain.okta.com, your-client-id, and your-client-secret with your actual Okta domain and credentials.
4. Define Access Policies
Create roles and grants to define access policies.
Creating a Role:
boundary roles create -name "admin-role" -scope-id "global" -description "Admin role with full permissions"
Creating a Grant:
boundary grants create -role-id "admin-role-id" -scope-id "global" -principal-id "user-id" -type"admin"
Replace admin-role-id and user-id with your actual role and user IDs.
5. Deploy Boundary in Production
For production deployment, use the HashiCorp Cloud Platform (HCP) to deploy Boundary with ease.
Steps:
- Log in to the HashiCorp Cloud Platform.
- Navigate to the Boundary section.
- Follow the deployment steps provided in the HCP portal.
Example Usage
Creating a Project and Target
- Create a Project:shCopy code
boundary projects create -scope-id "global" -name "example-project" -description "Example Project" - Create a Host Catalog:shCopy code
boundary host-catalogs create static -scope-id "project-id" -name "example-catalog" -description "Example Host Catalog" - Add a Host to the Catalog:shCopy code
boundary hosts create static -host-catalog-id "catalog-id" -name "example-host" -address "192.168.1.1" - Create a Target:shCopy code
boundary targets create tcp -scope-id "project-id" -name "example-target" -description "Example Target" -default-port 22 -session-connection-limit 10
Managing Sessions
- Start a Session:shCopy code
boundary connect ssh -target-id "target-id" - Terminate a Session:shCopy code
boundary sessions delete -id "session-id"
Automating with Terraform
You can also manage Boundary resources using Terraform. Here is an example Terraform configuration:
provider "boundary" {
// Configuration options
}
resource "boundary_scope" "example_scope" {
name = "example-scope"
description = "Example Scope"
}
resource "boundary_host_catalog" "example_catalog" {
scope_id = boundary_scope.example_scope.id
name = "example-catalog"
description = "Example Host Catalog"
}
resource "boundary_host" "example_host" {
host_catalog_id = boundary_host_catalog.example_catalog.id
name = "example-host"
address = "192.168.1.1"
}
resource "boundary_target" "example_target" {
scope_id = boundary_scope.example_scope.id
name = "example-target"
description = "Example Target"
default_port = 22
session_connection_limit = 10
}
FAQ:
Q: What is an easy way to allow access to applications and critical systems with fine-grained authorizations?
An easy way to allow access to applications and critical systems with fine-grained authorizations is by using boundary. Boundary is an identity-aware proxy that helps in managing privileged access management. It enables secure user access to hosts and critical systems without exposing your network.
Q: How does Boundary provide access to hosts and critical systems without exposing your network?
Boundary can be used to provide access to hosts and critical systems with fine-grained authorizations. Boundary also supports access configuration as workloads and discovery and access configuration, ensuring secure user access without exposing your network.
Q: What is Teleport and how does it facilitate remote user access?
Teleport is an open-source tool that facilitates remote user access by providing ssh access and privileged access management. It integrates with many others that support access control and allows secure user access to systems and applications.
Q: How can Boundary be used to manage access across clouds?
Boundary can be used to manage access across clouds by providing secure user access and privileged access management. It acts as an identity-aware proxy and allows access configuration as workloads, making it a powerful tool for multi-cloud environments.
Q: What is the benefit of using Boundary for access management?
Using Boundary for access management provides an easy way to allow access to applications and critical systems with fine-grained authorizations. It ensures secure user access and access configuration as workloads, making it an ideal solution for privileged access management.